A Global Financial Management Platform Detected 70%+ of Coordinated Fraud Rings with DataVisor’s UML
Discover how a leading financial management platform achieved $5.3M in annual loss savings and improved operational efficiency 10× with DataVisor’s AI-powered UML.


Company
A global financial management platform connecting 7+ million businesses, vendors, and payment providers.
Industry
B2B
Fintech
Use Case
Payment Fraud
Onboarding Fraud
ATO
Products
UML
Knowledge Graph
Case Management
Background
This case study examines a leading U.S. financial management and accounting platform supporting over 7 million SMBs that relies on fast, low-friction onboarding and secure payment flows across invoicing, payouts, and daily transaction operations.
As volume grew, coordinated fraud rings exploited onboarding and payment flows to run unauthorized transactions, funding exits, and account takeovers. Traditional defenses caught known patterns but missed new, fast-evolving attacks.
The platform partnered with DataVisor, using Unsupervised Machine Learning (UML) to detect fraud rings early, link related accounts, reduce loss exposure, and generate real-time alerts on suspicious activity.
Challenges
The fraud team began seeing a rise in incidents that appeared unrelated—isolated alerts tied to individual merchants, transactions, or accounts. Each case looked reasonable on its own, leaving no clear indicators of coordination. In reality, the platform was being targeted by a multi-path fraud ring engineered to mimic normal merchant behavior, making the activity hard to catch by rule-based tools.
How the Fraud Manifested
The operation used several subtle entry points:
- Payment fraud
Fraud occurred when fraudsters used stolen or fake payment methods to pay invoices or make purchases from legitimate merchants - Onboarding fraud
Fraudulent or fully fabricated merchants processing transactions through newly created accounts. - Account takeover
Compromised legitimate business accounts used for unauthorized actions that appeared trustworthy.
Why it was hard to detect
Individually, the merchants and transactions showed no obvious red flags. The fraud ring relied on rapid onboarding, fast fund movement, and behaviors calibrated to pass automated thresholds. Traditional systems flagged occasional anomalies but lacked the ability to connect them. The team could see isolated symptoms—but not the coordinated network behind them.
Solutions
To uncover what rules and traditional scoring could not see, the platform implemented DataVisor’s Unsupervised Machine Learning (UML)—a system designed to analyze all kinds of signals as a connected ecosystem rather than isolated events. With UML, every application, login, and payment was evaluated in relation to others, enabling the detection of coordinated behaviors that previously blended into the background. The knowledge graph, embedded directly into case management, stitched these signals together into clusters and networks, allowing investigators to make decisions at the ring level instead of case by case—dramatically improving both detection depth and operational efficiency.
How UML Detected the Fraud Ring
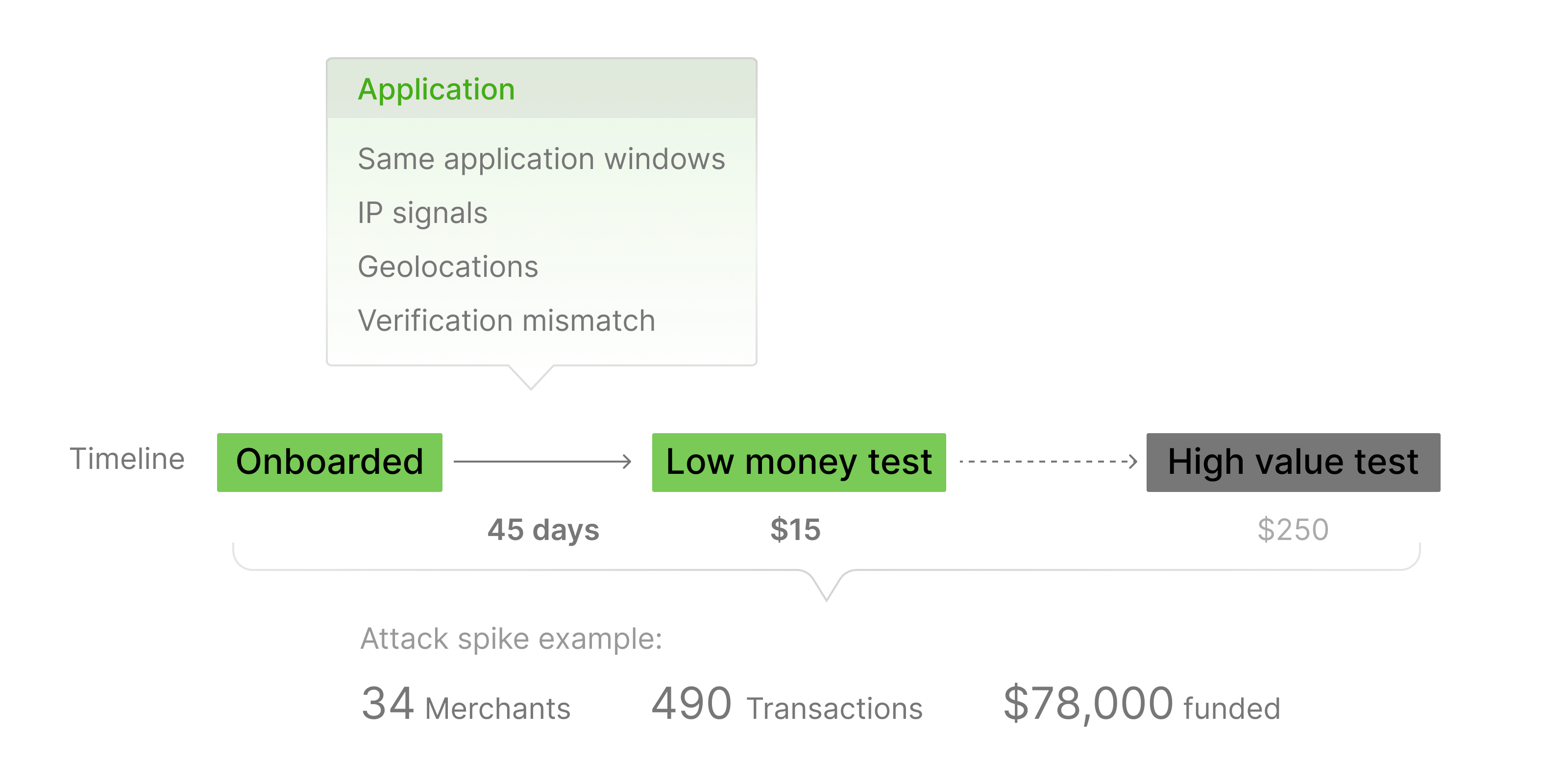
Once UML was deployed, the fraud activity that previously looked like isolated incidents began to reveal a very different story. By analyzing onboarding, identity, and transaction signals together, UML surfaced clusters of merchants whose behaviors were quietly synchronized: applications submitted during the same off-hour windows, rotating IP subnets, and business details that appeared unrelated yet originated from the same geographic pockets.
Application patterns
- Same application windows
Large groups of applications submitted during off-hours (early morning or late evening). - IP signal coherence
Subtle reuse and rotation of IP subnets. - Geolocation concentration
Businesses represented a variety of verticals but clustered geographically (notably a concentration in NY State). - Verification mismatch
Phones frequently verified while emails remained unverified; many owner emails used consumer domains or did not match business names or owner names.
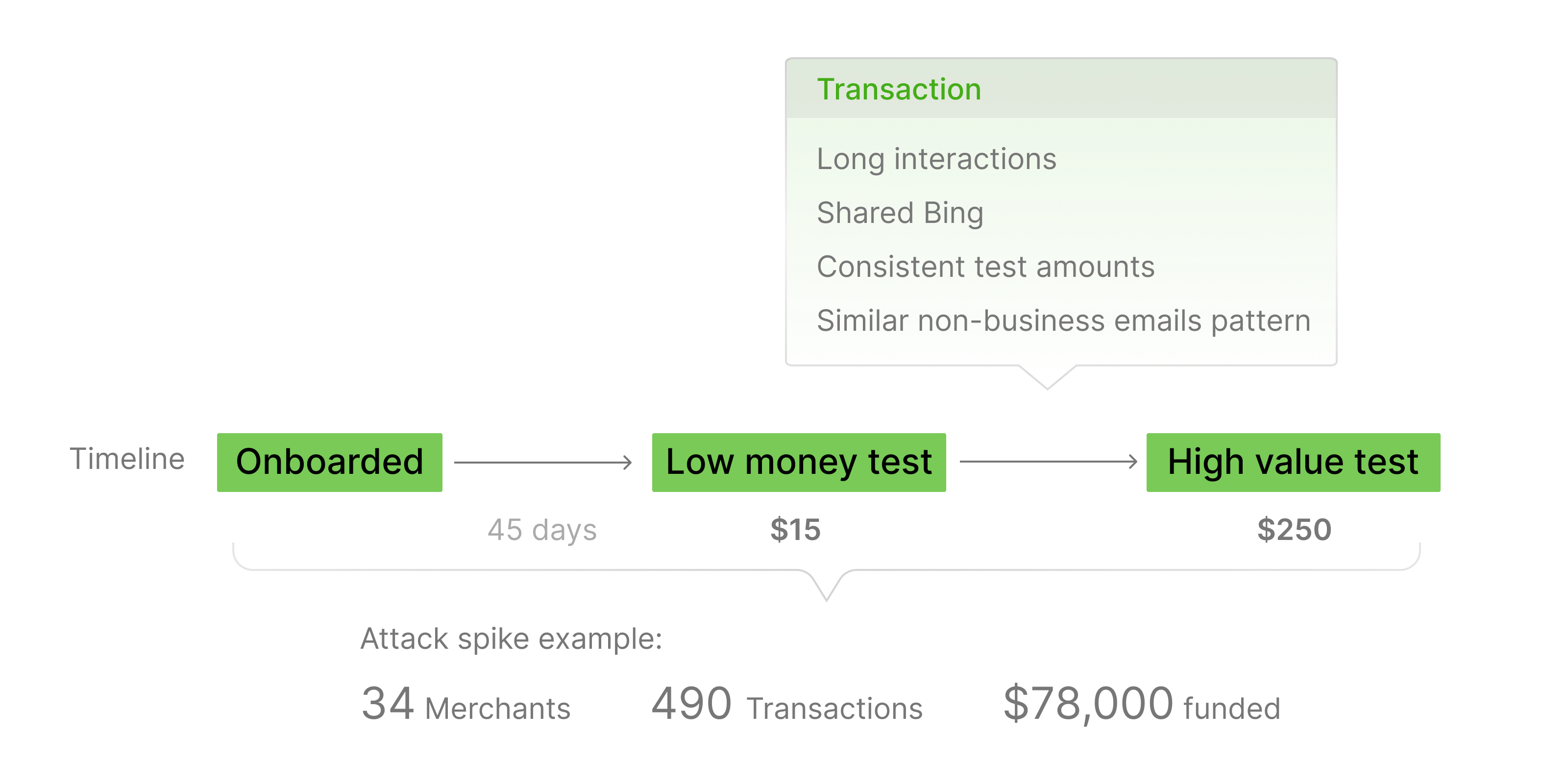
The transaction layer confirmed the pattern. Accounts that had lain dormant suddenly activated at the same time, ran tests with identical low-dollar amounts, then escalated to nearly identical higher-value transactions. Even email structures—non-business domains with repeating patterns—appeared across these clusters
Transaction patterns
- Long hibernation then activity
Accounts often stayed dormant ~45 days before first transaction. - Shared BIN pools
Card numbers rotated from the same BIN issuers, indicating coordinated card usage. - Consistent test amounts
Initial low-value test-amount (~$15) followed by repeated higher-value transactions (~$250), with many clusters showing similar transaction amount patterns. - Similar non-business email patterns
Emails with non-business domains or unusual patterns (random words, strings, or characters), often appearing across multiple accounts, suggesting automated or coordinated account creation.
Viewed individually, none of these signals were meaningful. Viewed together, they formed the fingerprint of a coordinated fraud ring.
How UML, Knowledge Graph and Case Management Together Transformed Fraud Operation Workflow
With these linkages exposed, the team’s workflow changed immediately. Instead of investigating scattered alerts, case management now surfaced entire networks of related accounts in a single view—supported by UML’s knowledge graph. High-risk rings were automatically rejected before losses accumulated, suspicious clusters were escalated as unified cases, and legitimate merchants moved through review far more quickly.
- Cluster-level detection replaced case-by-case review through knowledge-graph-enabled case management
- High-risk rings auto-rejected in real time
- Suspicious accounts escalated as a network, not individually
- Legitimate merchants received much faster decisions
What had once been a reactive hunt for anomalies became a proactive, network-level defense. UML allowed the team to see not just the symptoms, but the structure of the attack—and to act at the source.
Results
By adopting a more holistic and intelligent fraud defense, the platform improved early detection of coordinated attacks, streamlined operational workflows, and reduced friction for legitimate users. This enabled faster, more confident decisions across onboarding and payouts while strengthening overall risk posture and customer experience.
Fraud Reduction & Savings
70% +
Coordinated fraud detected early
$1.3M
Losses prevented in 3 months ($5.3M annualized savings)
Accuracy & Efficiency
0.92%
False positive rate
10X
Operational efficiency through cluster-level workflows
80%
Reduction in business payment clearing
Business Impact
- Meaningfully lowered systemic fraud risk
- Accelerated and streamlined onboarding and payout decision
- Seamless experience for legitimate users
70%+
Coordinated fraud detected in real time by UML
$5.3M
Annual Loss Savings
0.92%
False Positive Rate
80%
Reduction in business payment clearing time
Let’s Solve Fraud and Financial Crime—Together
Tell us a bit about your needs, and we’ll connect you with a fraud expert who can help tailor the right solution for your organization.