Digital Fraud Wiki
Your source for the latest fraud intelligence, insights, research, and commentary.
Device Fingerprinting
What is Device Fingerprinting?
Device fingerprinting is a process of collecting unique identifying information from an electronic device. It is also variously referred to as browser or machine fingerprinting. Device fingerprinting is commonly used for identity validation, fraud prevention, and digital advertising. The fingerprinting process makes it possible to track individuals as they browse websites and interact with mobile applications.
Organizations that use device fingerprinting for identity validation and fraud prevention collect and store numerous device identifiers. These identifiers are collected via a web browser, a mobile app, or both. Among the identifiers collected via a web browser are browser version, IP address, OS version, screen resolution, system fonts, and HTTP cookies. Identifiers collected via a mobile app include device ID, GPS or location, and Wi-Fi networks.
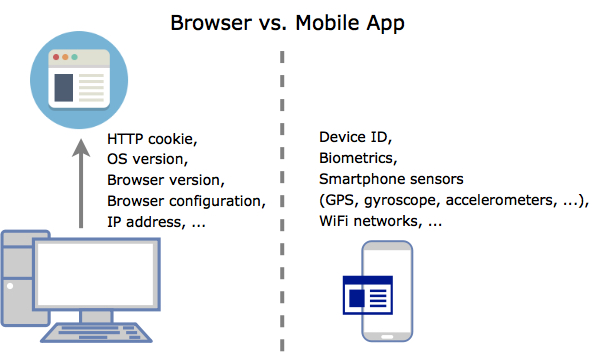
This graphic shows the identifiers used for fingerprinting when using a web browser vs. a mobile app.
Most organizations use device fingerprinting to identify users when they log into websites and mobile applications. Each time a user logs into a website or mobile app, the device fingerprint on file is matched with the characteristics of the device used at each login. Device fingerprinting is used not only to validate the identity of users but also to determine the level of risk when authenticating the login or a transaction.
What Should Organizations Know About Device Fingerprinting?
Device fingerprinting-based security measures are no longer effective because fraudsters continuously find ways to bypass them. Fraudsters use multiple approaches and techniques to bypass device fingerprinting protections, including stolen and synthetic identities, remote access trojans (RAT), and mobile device ID resets.
Device fingerprinting cannot detect users who create accounts using stolen or synthetic identities, and device fingerprinting is ineffective when it comes to fraudsters who use Remote Access Trojans. A RAT allows a fraudster to use the actual device of the fraud victim. The fraudster is not imitating the ID characteristics of the original device. So, device fingerprinting as an identity validation tool would be ineffective. Fraudsters also reset mobile device IDs and use emulators to mimic device IDs to bypass fingerprinting protections. Fraudsters can find device IDs available for purchase on dark web marketplaces. With a stolen device ID and previously recorded activity information from the real device, fraudsters can generate the same characteristics and identifying information as the original device.
To combat the evolving strategies fraudsters develop to bypass defenses such as device fingerprinting, organizations must implement multi-layered fraud prevention solutions that can keep up with malicious innovation and adapt to new techniques being used to bypass website login security measures.
In light of mobile’s continuing ascendance—In 2018, 52.2 percent of all website traffic worldwide was generated through mobile phones—it is especially critical organizations understand the limitations of mobile device fingerprinting. Using sophisticated techniques such as device flashing, bot accounts controlled by fraudsters can appear to originate individually from different devices and geolocations, just like legitimate users.
DataVisor Delivers Accurate Device Identification
DataVisor’s Device ID solution is expressly built to protect native mobile applications and provides complete visibility into mobile attacks by gathering real-time device fingerprints and detecting advanced device manipulation. It allows users to collect accurate and extensive mobile device fingerprints for both Android and iOS, and gather real-time information regarding device info, operating system, location setting, timestamp, languages, user agents, and more.
When used in combination with other DataVisor fraud prevention solutions and machine learning engines, the Device ID system enables proactive detection of known and unknown malicious attacks without the need for historical data. DataVisor Device ID draws on the power of proprietary unsupervised machine learning algorithms to collect device fingerprints to identify devices, detect manipulations, and deliver fraud scores with exceptional accuracy, empowering clients to take action with confidence.
Additional References
Blog: Mobile Fraud Gone in a (Device) Flash, DataVisor
Blog: Are Mobile Devices the Leading Target for Fraudsters?, DataVisor
Blog: Dealing with the Complexity of Fraud Attacks in Mobile Application Fraud, DataVisor
Source: Percentage of all global web pages served to mobile phones from 2009 to 2018, Statista